Activity Instance Management
When a user clicks “Join Application”, they expect to enter the same application that their friends are participating in. Whether the application is a shared drawing canvas, board game, collaborative playlist, or first-person shooter; the two users should have access to the same shared data. In this documentation, we refer to this shared data as an application instance.
instanceId is necessary for your application, as well as Discord, to understand which unique instance of an application it is talking to.
Using instanceId
TheinstanceId attribute is available as soon as the SDK is constructed, and does not require the SDK to receive a ready payload from the Discord client.
instanceId should be used as a key to save and load the shared data relevant to an application. This ensures that two users who are in the same application instance have access to the same shared data.
Semantics of instanceId
Instance IDs are generated when a user launches an application. Any users joining the same application will receive the sameinstanceId. When all the users of an application in a channel leave or close the application, that instance has finished its lifecycle, and will not be used again. The next time a user opens the application in that channel, a new instanceId will be generated.
Instance Participants
Instance Participants are any Discord user actively connected to the same Application Instance. This data can be fetched or subscribed to.Render Avatars and Names
Check out detailed documentation on where and how Discord stores common image assets here. Here’s a basic example for retrieving a user’s avatar and usernameRendering guild-specific avatars and nicknames
In order to retrieve a user’s guild-specific avatar and nickname, your application must request theguilds.members.read scope. Note, this only grants the information for that instance of the application’s user. To display the guild-specific avater/nickname for all application users, any info retrieved from guilds.members.read scope’d API calls must be shared via your application’s server.
Here’s an example of how to retrieve the user’s guild-specific avatar and nickname:
- Store the user’s access token on the application server
- Retrieve the user’s guild-specific avatar and nickname via the application’s server
- Serve all of the application’s avatar/nicknames via the application’s server
Preventing unwanted activity sessions
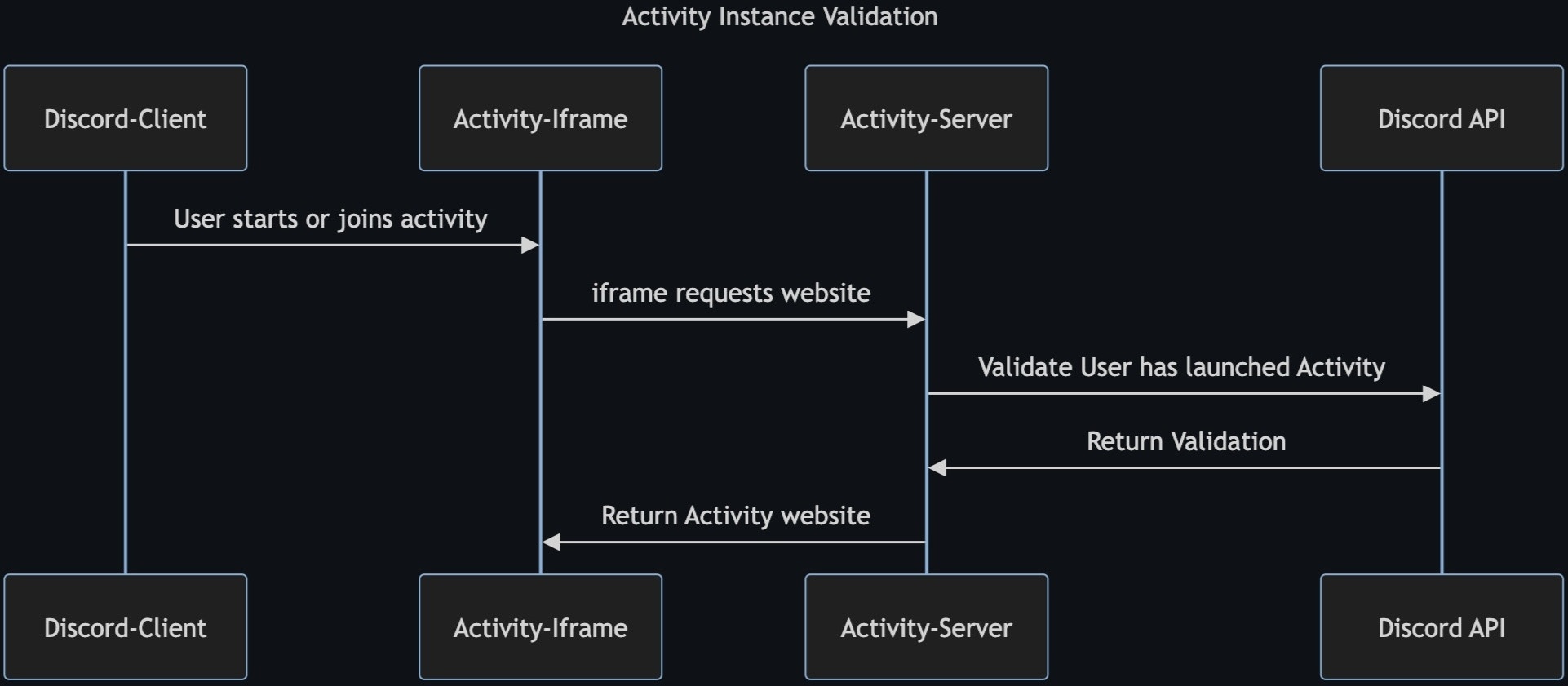
Activities are surfaced through iframes in the Discord app. The activity website itself is publicly reachable at<application_id>.discordsays.com. Activities will expect to be able to communicate with Discord’s web or mobile client via the Discord SDK’s RPC protocol. If a user loads the activity’s website in a normal browser, the Discord RPC server will not be present, and the activity will likely fail in some way.
It is theoretically possible for a malicious client to mock Discord’s RPC protocol or load one activity website when launching another. Because the activity is loaded inside Discord, the RPC protocol is active, and the activity is none the wiser.
Using the Activity Instance API
To enable an activity to “lock down” activity access, we encourage utilizing theget_activity_instance API, found at discord.com/api/applications/<application_id>/activity-instances/<instance_id>'. The route requires a Bot token of the application. It returns a serialized active activity instance for the given application, if found, otherwise it returns a 404. Here are two example responses:
Validating Proxy Request Headers
For apps that want additional security validation, Discord provides an optional proxy authentication system. When your embedded app makes requests through Discord’s proxy, each request can include cryptographic headers that prove the request’s authenticity. Each proxy-authenticated request is sent with the following headers:X-Signature-Ed25519as a cryptographic signatureX-Signature-Timestampas a Unix timestampX-Discord-Proxy-Payloadas a base64-encoded payload containing user context
401 error code.
Proxy authentication is entirely optional and provided as an additional security layer for apps that choose to implement it.
In the below flow diagram, we show how the server can deliver the activity website, only for valid users in a valid activity instance: